Blog
Your blog category
-
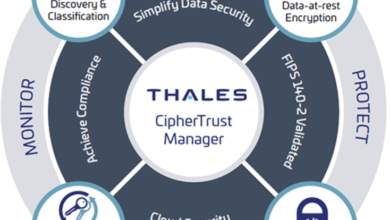
8138041015: Advanced Data Encryption Owner
The owner of 8138041015 stands at the forefront of data encryption technology, implementing sophisticated algorithms that safeguard sensitive information. This…
Read More » -

7252799543: AI-Powered Transaction Auditor
The 7252799543 AI-Powered Transaction Auditor represents a significant advancement in the field of financial auditing. By utilizing machine learning algorithms,…
Read More » -

7042282494: Quantum Security Architect
The emergence of quantum computing presents significant challenges to existing cybersecurity frameworks. Traditional encryption methods may become obsolete, exposing sensitive…
Read More » -

7023671919: Digital Privacy Consultant
7023671919 operates as a prominent digital privacy consultant in a time when personal data is increasingly at risk. Their approach…
Read More » -

7023047669: Automated Systems Engineer
Automated Systems Engineers are pivotal in optimizing automated processes within diverse sectors. Their proficiency in programming and system design enhances…
Read More » -

5747043062: Digital Signature Holder
The 5747043062 Digital Signature Holder represents a significant advancement in electronic document signing technology. Its integration of strong encryption and…
Read More » -

5715704136: AI Algorithm Supervisor
The role of the AI Algorithm Supervisor, designated by code 5715704136, is becoming increasingly critical in today’s technological landscape. This…
Read More » -

5714640382: Smart Contract Auditor
The emergence of 5714640382: Smart Contract Auditor highlights a critical shift in the blockchain landscape. Its systematic approach to identifying…
Read More » -

5702931143: Intelligent Systems Owner5702931143
The role of the Intelligent Systems Owner, designated 5702931143, is crucial in managing advanced automated systems within organizations. This position…
Read More » -

5592165530: Secure Machine Learning Operator
The 5592165530 Secure Machine Learning Operator represents a significant advancement in the realm of data protection. By leveraging sophisticated anomaly…
Read More »
